How State-Sponsored Information Operations Divide and Conquer
By Joshua Uyheng
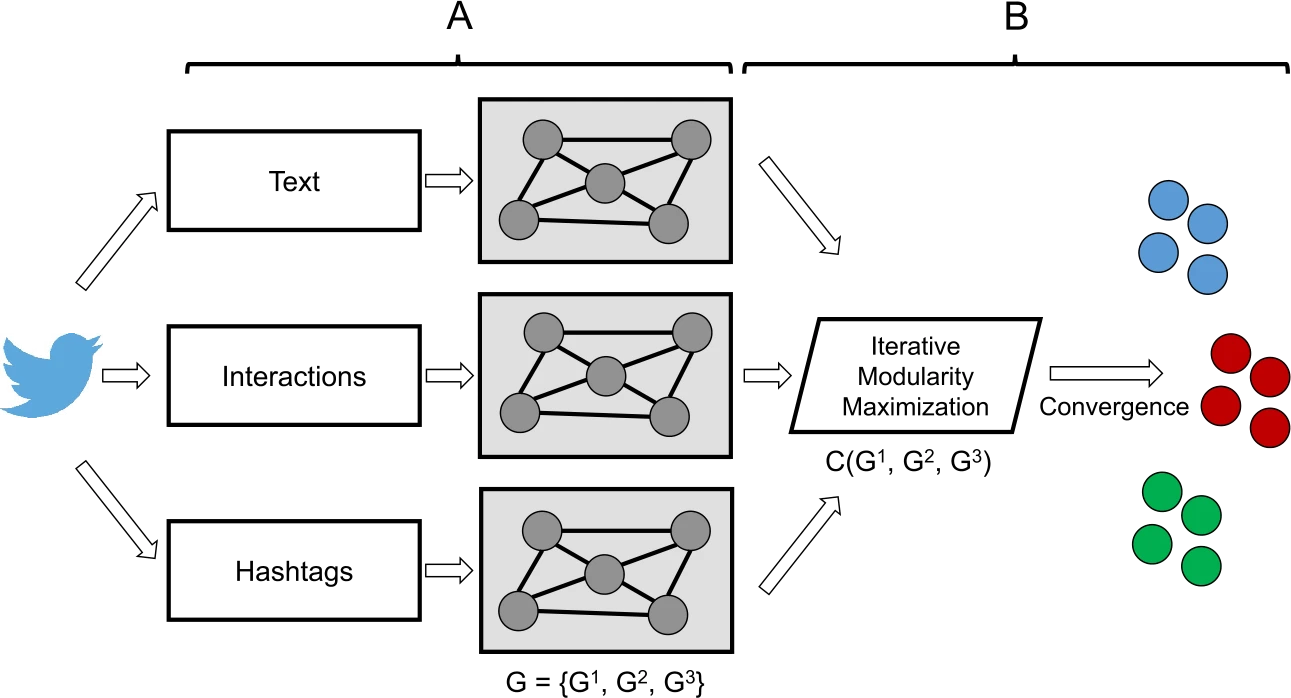
Image caption: Graphical depiction of the MVMC technique used in this study. In the first step of the method, A, a graph representation is learned for every view of the data. In the second step, B, the view graphs are all collectively clustered to produce a single clustering across all of the views. Figure adapted from prior foundational work on MVMC.
Tags: information operations; multi-view modularity clustering; state-sponsored disinformation
Recent Publication:
Uyheng, J., Cruickshank, I. J., & Carley, K. M. (2022). Mapping state-sponsored information operations with multi-view modularity clustering. EPJ Data Science, 11(25). https://doi.org/10.1140/epjds/s13688-022-00338-6 URL: https://epjdatascience.springeropen.com/articles/10.1140/epjds/s13688-022-00338-6
It’s no secret that government officials and nation-states use social media platforms to manage their international reputation. Individuals do so, and so do brands and businesses, to great effect. With the speed and scale that Twitter and Facebook allow for information dissemination and collective dialogue, it’s no wonder that governments, too, use these websites to amplify their agendas, grow public support, and project images of power and competence on a global stage.
Yet not all social media activity by state actors is created equal. It’s one thing for a savvy ambassador to crack a viral joke online, and quite another for a regime to fund and coordinate an army of inauthentic accounts to manipulate public opinion and quash dissent.
Such state-sponsored information operations have become the subject of major academic research and public controversy especially in the past five years. Who could forget the relentless news coverage of the Russian Internet Research Agency (IRA) or Cambridge Analytica during the 2016 US Presidential Elections? All around the world, journalists and researchers have likewise exposed government involvement in click farms, hate apps, and paid trolls.
But how exactly do state-sponsored information operations achieve their influence over public conversations? Malicious operators don’t trigger shifts in people’s beliefs and actions just by infiltrating online conversations. Information actors engage in a particular set of online behaviors to shape online narratives and networks. Moreover, they do so in a manner that is both coordinated and differentiated to accomplish their strategic objectives.
In our recently published paper, we develop a framework for systematically identifying these strategies using a new network science methodology known as multi-view modularity clustering (MVMC). Through this method, we automatically parse a complex Chinese state-sponsored information operation into distinct sets of actors engaged in unique aspects of the overall campaign. Beyond revealing the tactical contours of online Chinese propaganda in particular, our work also demonstrates the value of seeing information operations in general not as monolithic black boxes, but as systems with moving parts designed to divide and conquer.
Information Operations as Multi-View Networks
The crux of our method lies in seeing information operations through the lens of multi-view networks. A network in its classical sense refers to a set of nodes (e.g., Twitter accounts) connected by edges (e.g., retweets). A multi-view network refers to a system where nodes can be connected with multiple types of edges (e.g., retweets and shared hashtags).
One value of a network approach is that mathematical relationships in network structures point to meaningful patterns in the phenomena they’re designed to represent. Clusters in a Twitter retweet network, for example, may indicate smaller communities of accounts that like to amplify each other’s messages. For a network of Twitter accounts connected by shared hashtags, clusters may point to groups that are likely discussing a topic in a similar way.
Here then is the innovation: when we cluster multi-view networks with MVMC, we derive communities of agents connected across multiple types of relationships. This is particularly useful for breaking down state-sponsored information operations into subsets of the campaign that not only talk about the same thing, but also work together to spread this information in a similar way.
In other words, MVMC can make sense of an otherwise undifferentiated collection of state-sponsored accounts into smaller units working together to accomplish distinct strategic functions. That’s exactly what we did with the Chinese state-sponsored accounts disclosed by Twitter in June 2020.
Three Strands of Chinese Online Campaigns
Through MVMC, we found three overarching themes across tactical subunits of the Chinese state-sponsored campaign: attacking individual targets such as Guo Wengui, attacking collective opposition such as the Hong Kong pro-democracy protestors, and upholding national solidarity amid the COVID-19 crisis. This revealed a broader Chinese campaign to bolster a unified and harmonious national identity while demonizing people and groups whose existence and activities contradicted this ideal.
From a narrative standpoint, account clusters focused on Guo Wengui and Hong Kong pro-democracy protestors took similar approaches to paint them as self-interested, untrustworthy, and deserving of punishment. Using negative-sentiment and abusive language, they highlighted links between Guo Wengui and right-wing conspiracy theorists, while Hong Kong protestors were framed as violent actors dangerous to the safety of Hong Kong.
From a network standpoint, these messages were also pushed out in a relatively decentralized fashion, with no clear leader-follower structure. Instead, a focus on replies and mentions indicated that these accounts engaged in real-time exchanges to project an organic backlash against these individual and collective targets.
By contrast, to perform solidarity during the pandemic, the accounts for COVID-19 messaging tended to use more positive-emotion language and used hashtags that encouraged the people of China to come together and survive the crisis together. These messages, by contrast, were amplified in a much more hierarchical fashion, with a preponderance of retweets coming from more centralized opinion leaders. These tactics thus not only communicated unity through the content of their messages, but also through the synchronized process by which they were disseminated.
Break Them Down to Break Them Up?
Taken together, our findings reveal the tactics which constitute the Chinese playbook for influencing social media conversations. More pointedly, we demonstrate the elements of the Chinese carrot-and-stick strategy of punishing opponents and bolstering national identity.
Yet beyond exposing these specific maneuvers, we also shed light on which facets of its international reputation China is most concerned with protecting and promoting online. These deeper insights may thus be useful in a diplomatic and international relations context that extends far beyond cyberspace.
This work also demonstrates the usefulness of a multi-view network approach to understanding state-sponsored information operations writ large. While it is certainly valuable to address these campaigns comprehensively, breaking them down into their component parts may also allow for more holistic and responsive policy measures tailored to distinct tactics.
From this standpoint, perhaps these campaigns can be divided and conquered, too.
