Malware
Malware, short for malicious software, is a term for viruses, worms, trojans and other harmful computer programs that scammers use to cause damage and gain access to sensitive information on a single computer, server, or computer network.
WHAT TO DO IF YOU HAVE MALWARE
Removing malware can be extremely difficult. Malware, by design, will try to make itself almost impossible to remove. The only guaranteed way to remove malware is to reformat your computer and reinstall - which will delete all of your files. This is a reason why backing up your data is crucial. Hard drive reformatting is a stressful enterprise without a good backup, but a minor time annoyance otherwise.
In addition to restoring your computer or device to a previous state - you should change your passwords.
TYPES OF MALWARE
Adware
Adware is essentially abusive advertising software. This includes pop-up ads and "bundled" software such as browser toolbars. Some adware is innocuous advertising, but other instances of adware are highly manipulative and create an open door for other malicious programs. It is never a good idea to knowingly install or click on adware. When downloading software, be sure it is not also asking permission to download additional software on top of the desired product. When browsing be sure to use pop-up or script blockers.
Ransomware
Ransomware encrypts a computer's data so that it is inaccessible without a password. The ransomware distributor will then demand a certain amount of money, sent through an anonymous method such as bitcoin, in order to decrypt the computer data. There is oftentimes a time limitation for payment. After this time limit, the computer's files will be deleted. There is no way of knowing for sure if the criminal will decrypt your files after paying the "ransom". The best way to recover from ransomware is to recover your data from a backup. This is why it is essential to create strong backups of your data, especially the data that is crucial to your job.
Rootkit
Rootkits are designed to remain hidden on a victim’s computer while providing the scammer the ability to remotely control the computer and potentially steal sensitive information and cause significant damage. Rootkits can include viruses, worms, and Trojan horses and depending on the type, can perform remote modifications to the computer, steal personal information, execute malicious files, and potentially create bots.
Spyware
Spyware will record activity on a victim's computer and transmit the data elsewhere. This includes login information, browser history, and potentially other information. Spyware will try to remain hidden so that it won't be removed. It can also modify security and network settings.
Trojan Horse
A Trojan Horse malware will trick a user into downloading malicious software. A Trojan Horse will often disguise itself as an innocent file to download, but instead will provide someone else access to the computer where the scammer can steal information and/or install additional malware such as ransomware.
Virus
Viruses are malicious programs that will attempt to spread from machine to machine. They can attach themselves to files and programs shared between computers in order to infect as many machines as possible.
Worm
Worms are spread through networks, finding security vulnerabilities in programs and operating systems to infect machines. A computer worm has the ability to damage a computer, steal or delete information, and install bots.
EXAMPLES OF MALWARE
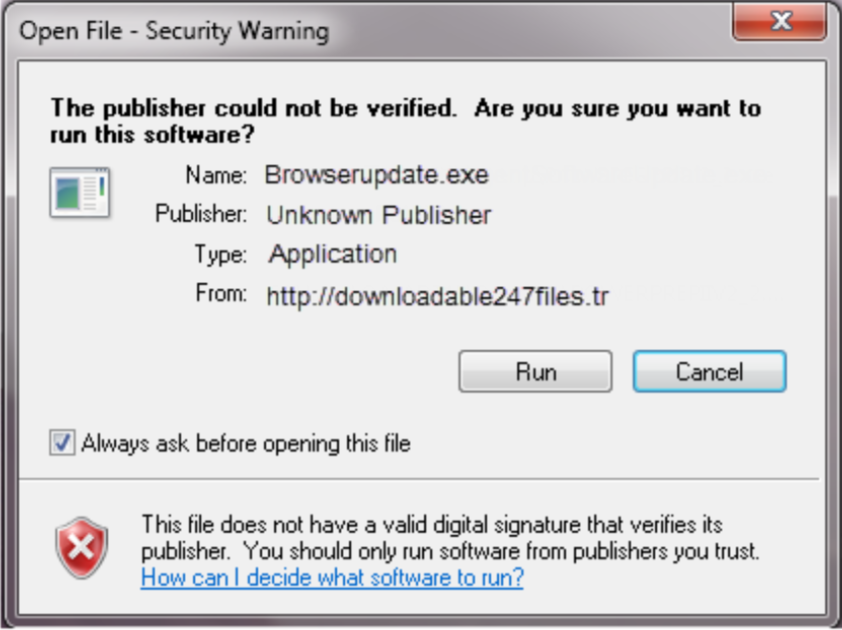
In this example, the malicous file is seeking human permission to execute (.exe) or run. Analyzing the Publisher and the From can help to determine if the file is malicious. In this scenario, the file has an "Unknown Publisher" and the "From" address doesn't look legitimate.
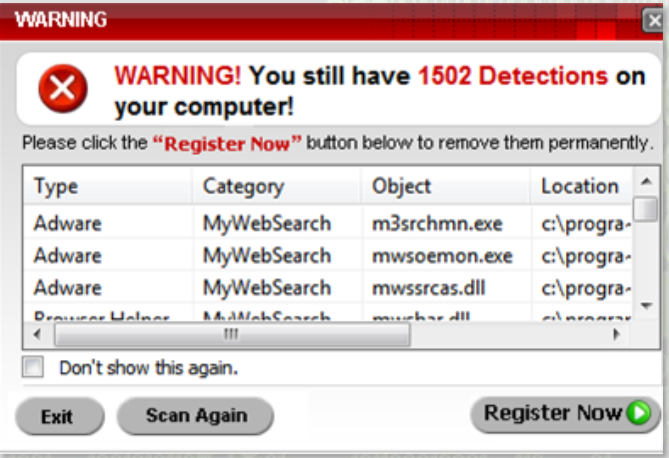
If you receive a suspicious Pop-up Warning on your computer, prompting you to register for a computer scan, it may mean that you already have a form of malware on your device. You can use the Task Bar to force quit this pop-up and immediately run a computer scan using your trusted antivirus software.
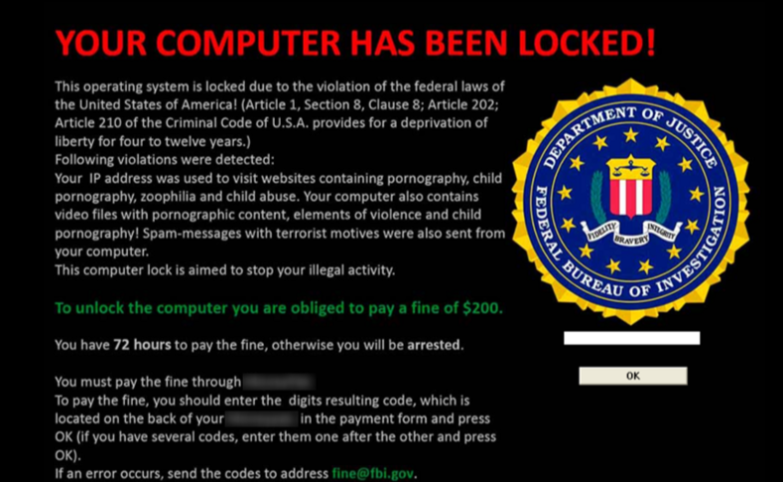
If your computer screen suddenly shows an official looking message from a government agency suggesting that your system is in violation of a federal law and requires a form of payment to unlock the device, it is most likely a form of ransomware. If you receive this message on your device, disconnect from the network and contact the Information Security Office.
ANTI-MALWARE SOFTWARE
Click here to download CrowdStrike.
For more information please visit the Computing Services - Secure your Computer and Devices.