Social Engineering: Pretexting and Impersonation
Pretexting is a form of social engineering where a criminal creates a fictional backstory that is used to manipulate someone into providing private information or to influence behavior. Criminals will often impersonate a person of authority, co-worker, or trusted organization to engage in back-and-forth communication prior to launching a targeted spear phishing attack against their victim. Criminals conduct extensive research on a target in order to create a credible story to help build rapport and establish trust.
To help establish credibility, criminals will use leaked personal information from previously disclosed data breaches, as well as the Internet to learn about their potential victims. Some things criminals may use to establish credibility in a pretexting attack is the target’s job title, office location, work history, business relationships, and personal information such as home address, phone number, date of birth, last 4-digits of a social security number or credit card.
Use the following tips to ensure that you do not fall victim to a pretexting social engineering attack:
- Limit personal information that is shared online.
- Regularly review search results for your name on an Internet search engine. Request to have personal information removed from any public sites.
- Use a trusted channel to verify the phone number or email address of an unusual message.
- Always be suspicious of unsolicited "urgent" requests.
- Never provide passwords, SSNs, personal/confidential information where you cannot be sure who you are talking to.
- Don't click on links in email, instead navigate to a trusted webpage.
- Don't open unexpected attachments.
- If a company you do business with is requesting information, inform them that in order to protect yourself against identity theft, you will need to reinitiate contact with the company through a trusted channel.
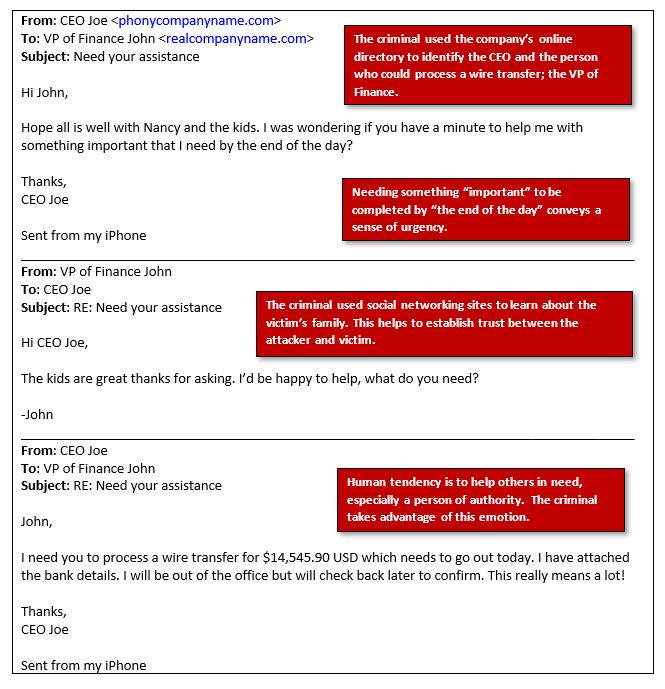
Example of a Pretexting Social Engineering Attack