
Safekeeping Faces at the Edge
Recently, in an incident at Madison Square Garden (MSG), face recognition technology was used to exclude concert goers who were employed by law firms suing the venue. This incident shows that rapid advances in computer vision and face recognition have gotten ahead of our ability to use them wisely – or, even agree on how to use them. It raises major questions about face recognition technology: who gets to use it, for what purposes, on what populations, whether the informed consent of that population is required, and how unauthorized use can be prevented. Many people would see the MSG case as unethical and forebodingly creepy – and one that warrants greater controls.
As so often happens, we can create technology far faster than our social and legal systems can adapt. And, as is so often necessary, we must adapt technology to meet compelling societal needs as they emerge. Current efforts around explainable AI are one recent example of this adaptation requirement. For the ethical questions raised by face recognition, a more direct intervention to align with emerging norms and policies will likely be required. But, there are legitimate uses for the implicated technologies. Interventions shouldn’t excessively impede these legitimate uses.
We started the Silent Witness project at the Living Edge Lab in anticipation of these requirements. We believe that, while norms and policies will vary around the world, four computer vision technology principles will be common.
- Technology and data use must be restricted to authorized and authenticated users.
- However, authorized users should be readily able to access the technology for legitimate uses.
- Data should be closely held near the point of origin to limit the perimeter of attack and prevent leakage.
- Data should be protected at-rest and in-motion and only the minimum amount of data required should ever be decrypted for use.
Silent Witness explores ways to efficiently implement these principles in video surveillance use cases like the MSG case. We propose silent witnesses – edge-based cloudlets with substantial local video storage (see below). A silent witness collects data from surveillance cameras and stores it locally – encoded and encrypted – without ever examining it or forwarding it elsewhere. Silent witnesses only allow access with appropriate keys issued by a trust authority and only for a data subset authorized by, say, a valid search warrant.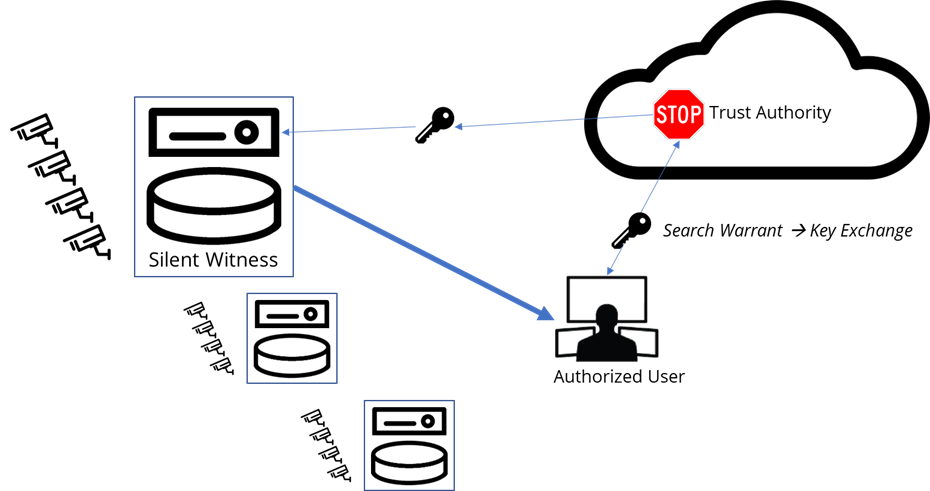
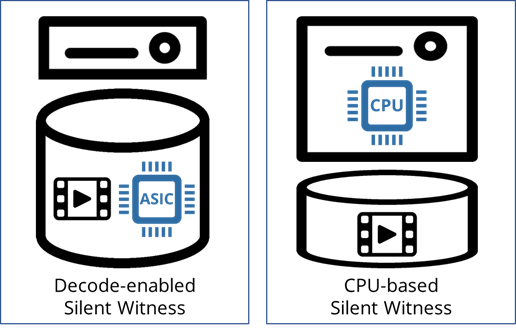
Since this approach precludes creating an index of the video as it arrives, an authorized search requires rapid decryption, decoding, and discarding of uninteresting objects (e.g., video frames without faces). The results are then presented to the authorized user. Our work explores ways of making this process efficient for the user and the system in the context of an object classification use case (detecting red buses in traffic videos). From the system’s perspective, the workload is video decode intensive and, because the content is likely to be distributed across many disks, we did an experiment to see if embedding a video decode ASIC in the storage system directly would improve the efficiency of the overall system (see figure below). Efficiency in this case is a complex trade-off between the efficiency of decoding in the ASIC or in a host CPU and the data transfer throughput between them. In our experiment, we found an up to 3.7X improvement system throughput by embedding video decoding in the storage system.
While these are early days in society’s progress toward ethical use of computer vision and face recognition, it is not too early to begin understanding how these technologies must adapt for our needs. We believe that the emergence of edge computing has significant ramifications for traditional privacy and security technologies and expect to continue our work in this domain in the coming years. For more information on Silent Witness, visit us at the Living Edge Lab website, read the IEEE Micro paper or the CMU Technical Report.
- Satyanarayanan et al., "Accelerating Silent Witness Storage," in IEEE Micro, vol. 42, no. 6, pp. 39-47, 1 Nov.-Dec. 2022, doi: 10.1109/MM.2022.3193048.
- Feng et al., “Improving edge elasticity via decode offload,” Schl. Comput. Sci., Carnegie Mellon Univ., Tech. Rep. CMU-CS-21-139, Sep. 2021. [Online]. Available: http://reports-archive.adm.cs.cmu.edu/anon/2021/CMU-CS-21-139.pdf