March 2018 Phishing: Security Alert on You Account
This past weekend, a targeted phishing e-mail was sent to campus community members. This phish presented a screen that looks like the CMU web login page. If you had entered your credentials, the attackers attempted to log into Workday, but were luckily foiled by Duo, our two-factor authentication.
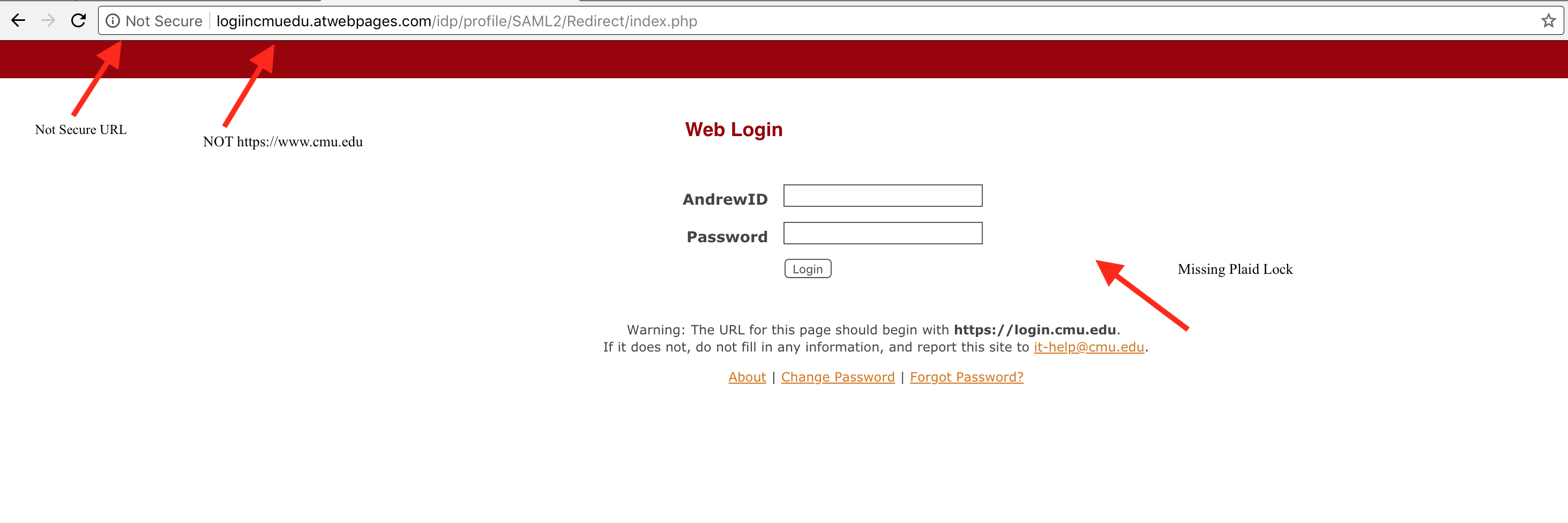
Besides the phishing e-mail itself, there were three things about the "login page" that would indicate that it was not a legitimate page. Two items may or may not be used in subsequent phishing, as they are easy to replicate correctly. The third item, the URL is more difficult to replicate correctly, and should be relied upon in the future.
First, the web site is not secure - meaning it is not using HTTPS. Chrome helpfully tells you that the site is "Not Secure" in the left hand side of the URL/address bar. All other browsers will alert you as well. Just because a site does not say "Not Secure", does not mean that it is a phish. It is possible to create an https site that will validate to most browsers without complaint.
Second, this particular fake site missed the plaid lock that is seen on our legitimate web site. This is extremely easy to replicate and the existance of the plaid lock does not mean that the site is legitimate.
Finally, The URL is not https://login.cmu.edu. Please, always look at the URL/location bar to check that you are indeed on https://login.cmu.edu. This is the single best indicator of whether a site is legitimate or not. if you don't see https://login.cmu.edu in the location bar, please do not enter your credentials and notify iso-ir@andrew.cmu.edu immediately.