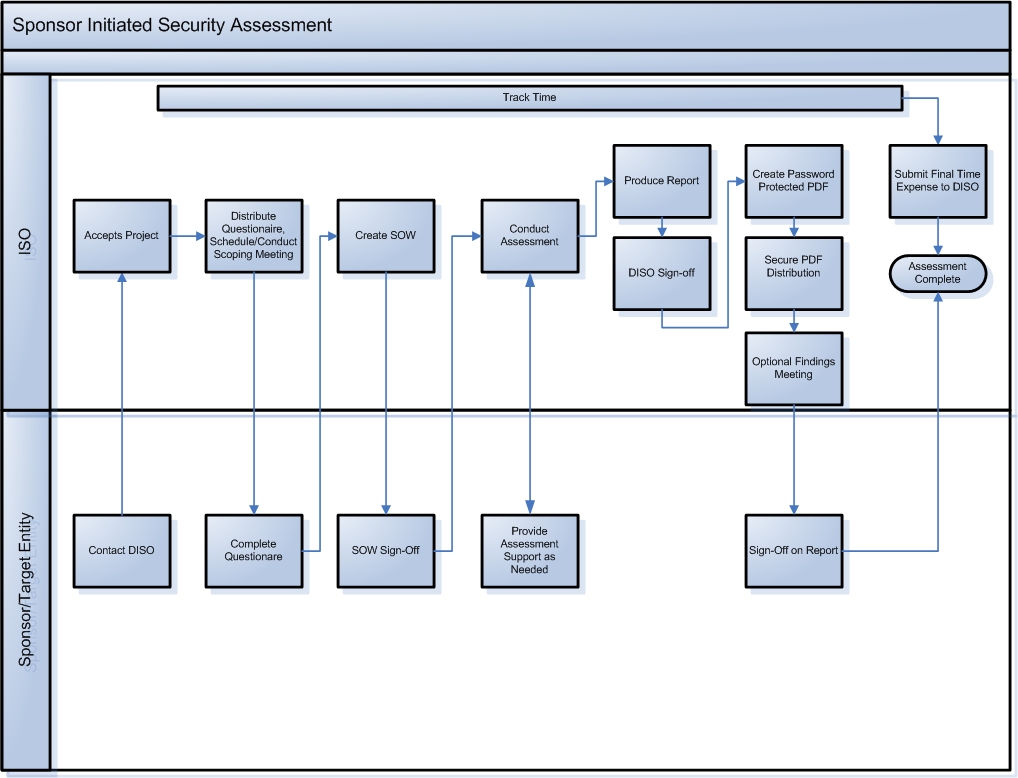
Security Assessment Process
The Information Security Office has created a simple process around security assessments to provide clarity and consistency. The process is as follows:
- Complete the Guidelines for Data Protection Self-Assessment Spreadsheet, answering all questions as applicable.
- Contact ISO at iso@andrew.cmu.edu
- ISO accepts the project
- Security Assessment Questionnaire is completed by the customer
- Scoping/Kick-off meeting is held. The goal of the Scoping/Kick-off meeting is to determine what type of assessment is appropriate, the scope of the assessment, a timeline for completion and contact information. A Statement of Work is produced as a result of this meeting and is signed by ISO and the customer.
- Assessment is scheduled (project end date also noted)
- Assessment is performed during agreed upon times. ISO will remain in contact with the customer throughout the assessment. In the event that ISO finds vulnerabilities that present an immediate security risk, the finding will be immediately communicated to the customer.
- Assessment report is produced and reviewed internally by ISO staff
- Assessment report is distributed to customer and review meeting is scheduled
- Wrap-up meeting is held where detailed findings are presented
- ISO and customer sign-off on results
This process is also illustrated in the following diagram.
Click for an enlarged view